top of page
Welcome to AI Insights & Cyber Alerts!
Empowering Leaders to Know, Grow, and Win.

Designed for forward-thinking business leaders, our blog equips you with the knowledge to drive innovation, reduce risks, and elevate customer experiences. At Nadicent, we cut through complexity to deliver clear, actionable insights, helping you navigate AI and cybersecurity with confidence and ease.
No fluff, just the insights you need to succeed.
Start Exploring Insights & Alerts Now!
Search


Admin
Mar 25, 20242 min read
Malware Downloads From Harmless Word Document
You have heard it over and over and likely, your reaction is “Yes, I know. Don’t enable macros in Microsoft documents or spreadsheets.”
12 views0 comments


Admin
Mar 25, 20243 min read
What Is The Price Of The Average Data Breach? Awareness Training May Be The Key To Prevention
The price tag for a data breach went up this year, way up.
10 views0 comments


Admin
Mar 16, 20242 min read
Storing Passwords In Your Browser…It’s Convenient, BUT Very Risky Too
Looking deeper into RedLine Stealer shows that the malware is capable of stealing more than passwords from browsers.
5 views0 comments
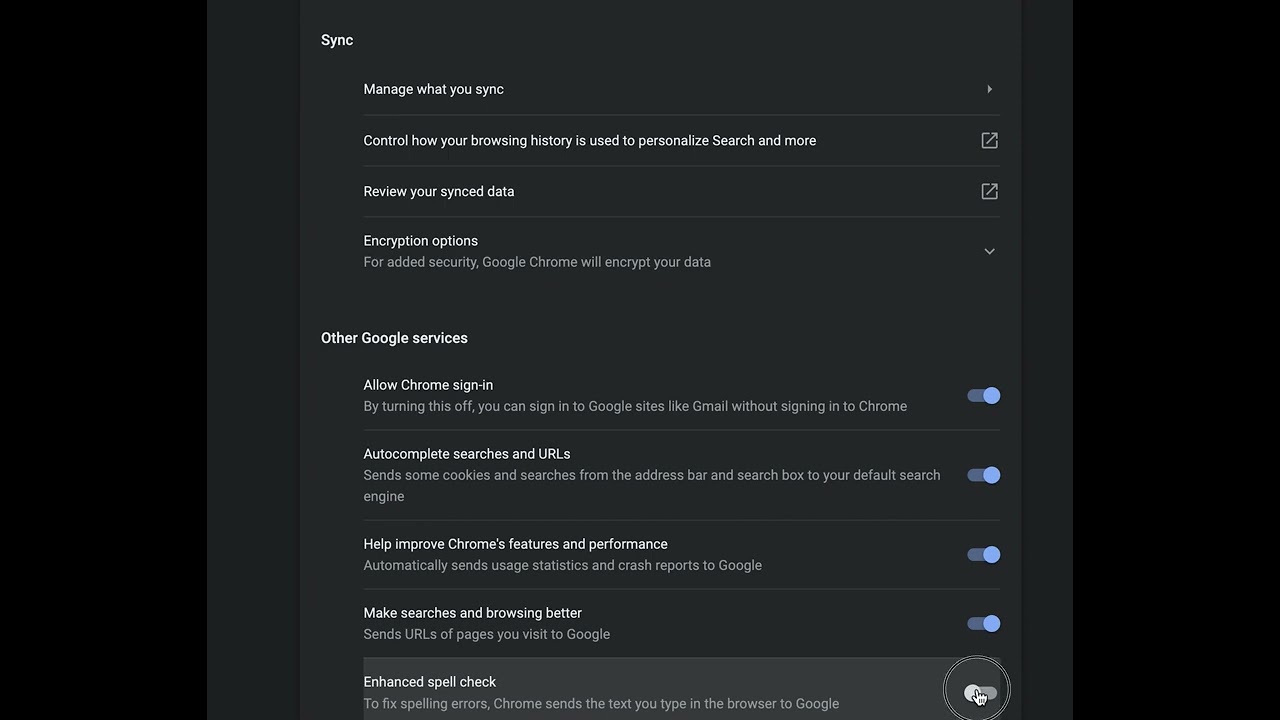

Admin
Mar 16, 20242 min read
How Using Your Browser’s Spell-Check Is “R-I-S-K-Y” For Your PII
No one wants to write an email or other document with spelling errors or bad grammar.
9 views0 comments


Admin
Jan 28, 20242 min read
Spyware Pop-Up Danger – 4 Words NOT To Click
When it comes to our personal online safety, sometimes knowing what NOT to do is as important as doing the smart thing.
3 views0 comments


Admin
Jan 28, 20242 min read
Downloading Some Apps May Get Your Device All Mixed Up
Over the past few years, we have all been discouraged from mixing with others, for fear of catching a nasty virus.
3 views0 comments


Admin
Jan 28, 20242 min read
Ransomware Attacks Drop 25% But That's Not The Whole Story
There’s news about ransomware getting mixed reactions from everyday users and businesses alike.
3 views0 comments


Admin
Nov 27, 20233 min read
It's Back...Again! Shopping Season Cybersecurity Tips
Unfortunately, all the deals also mean the cyber thieves are lurking around trying to make a profit off everyone else’s holiday cheer.
4 views0 comments


Admin
Nov 27, 20232 min read
Gootloader Grazes Legitimate Websites For Victims
When it comes to damaging malware, Gootloader has made a name for itself.
3 views0 comments


Admin
Oct 29, 20232 min read
Office 365 Users Warned – Don’t Give Email Permissions To Bogus Upgrade App
Email phishing campaigns involve a variety of hacker goals, most of which want you to install some type of malware on your device.
4 views0 comments


Admin
Oct 29, 20232 min read
Firewall vs. Antivirus: What’s the Difference?
In today's interconnected world, cybersecurity is more important than ever.
4 views0 comments


Admin
Oct 1, 20232 min read
Online Banking Risks – How Financial Institutions And Customers Partner For Better Security
If you think about it, the financial services sector has gone through significant changes since horse-drawn wagons delivered money to banks.
3 views0 comments


Admin
Oct 1, 20233 min read
QR Code Scanning Scams – How To Use QR’s Safely And Securely
In our never-ending pursuit of info-quick technology, QR (quick response) codes have found a huge following.
6 views0 comments


Admin
Oct 1, 20232 min read
Cybercrime Is Costly; Organizations Urged To Re-evaluate Cybersecurity Strategies
The cost to companies due to a data breach can bankrupt a business.
2 views0 comments


Admin
Oct 1, 20232 min read
Realst Malware Preying on Mac Users Through Fake Blockchain Games
A new cybersecurity threat has surfaced, ominously dubbed Realst.
4 views0 comments


Admin
Sep 10, 20232 min read
By All Means, Save Princess Peach; But Not By Playing This Game
Would you like to play a game?
3 views0 comments


Admin
Aug 5, 20232 min read
Office 365 Users Warned – Don’t Give Email Permissions To Bogus Upgrade App
Email phishing campaigns involve a variety of hacker goals, most of which want you to install some type of malware on your device.
4 views0 comments


Admin
Aug 5, 20232 min read
Firewall vs. Antivirus: What’s the Difference?
A successful attack can result in the loss of sensitive data, financial damage, and reputational damage.
4 views0 comments


Admin
Apr 30, 20232 min read
Gootloader Grazes Legitimate Websites For Victims
When it comes to damaging malware, Gootloader has made a name for itself.
4 views0 comments


Admin
Apr 30, 20232 min read
Firewall vs. Antivirus: What’s the Difference?
In today's interconnected world, cybersecurity is more important than ever.
3 views0 comments
bottom of page