Info-Stealing Families Increase Break-ins To Your Corporation
- Admin
- Oct 1, 2023
- 3 min read
Published: September 03, 2023 on our newsletter Security Fraud News & Alerts Newsletter.

The analysis of approximately 20 million information-stealing malware logs has unveiled that infiltration of such threats into business environments is spiking rapidly. And it’s not just one family of malware doing this either, but a whole bunch of them. That’s according to research by the security company, Flare, in a recently released report.
Before we get into the nitty-gritty, let's talk about a few ways everyone can help out their organization.
Here’s how to help at the corporate level:

Educate Employees: Provide comprehensive cybersecurity training to employees to raise awareness about the dangers of downloading software from untrusted sources and using personal devices for work-related activities.
Implement Strong Security Measures: Employ robust security solutions, including antivirus software, firewalls, and intrusion detection systems, to protect against potential malware threats.
Require Multi-Factor Authentication (MFA) for network access: Enable MFA wherever possible to add an extra layer of security, making it harder for cybercriminals to gain unauthorized access even if credentials are compromised.
Regularly Monitor and Review Logs: Monitor system logs and regularly review access logs to detect any suspicious activity or unauthorized access attempts promptly.
Keep Software and Applications Up-to-Date: Ensure that all software, including operating systems and applications, is kept up-to-date with the latest security patches and updates to minimize vulnerabilities.
Enforce Strong Password Policies: Implement and enforce strong password policies that require complex passwords and regular password changes.
Limit User Privileges: Assign the least privilege principle, granting users access only to the resources necessary for their specific roles, reducing the potential damage from a successful breach.
Here’s what individuals can do:

Avoid using personal devices for logging into social media or other personal accounts when on the corporate network.
Install anti-virus/anti-malware software and apps on all of the devices you use when connected at work. Keep all of it updated at all times.
Limit what information you post to the Internet about your role at work. Make it as generic as possible, or don’t list anything at all, so that you are less likely to be targeted. This is particularly important if you work in a role where you access financial accounts and information or personal identifying information about employees.
Enable MFA/2FA for all logins when it’s available. If you have a choice among several ways to do this, choose email as the last option. A hardware key or authenticator app will serve as better choices.
Stay on top of the latest cybersecurity threats and keep your eyes peeled for phishing threats. Don’t click attachments, images, or links in messages that you are not expecting to receive, are from unknown senders, or make you feel like they are too urgent to take a minute to think about. That’s always a big red flag.
Lastly, avoid commonly used infection channels such as clicking Google Ads, watching YouTube videos, and reading Facebook and other social media posts when on the corporate network.
Now on to the details. Information stealers, or info-stealers, are malicious software designed to pilfer data from various applications, including web browsers, email clients, instant messenger apps, cryptocurrency wallets, FTP clients, gaming services, and pretty much anything else you can think of. The stolen data is packaged into "logs" and most often either utilized by threat actors in attacks performed against all of us or sold on cybercrime marketplaces, so someone else can do that.
A malware family is a grouping of malware that employs the same tactics, has the same characteristics, and sometimes is developed by the same authors. The main information-stealing families are offered to cybercriminals through a subscription-based model (malware-as-a-service or MaaS, for example), allowing malware campaigns to do their evil deeds more quickly and easily than if someone were always writing them from scratch. While these threats historically targeted internet users downloading software from dubious sources, they are now impacting corporate environments.
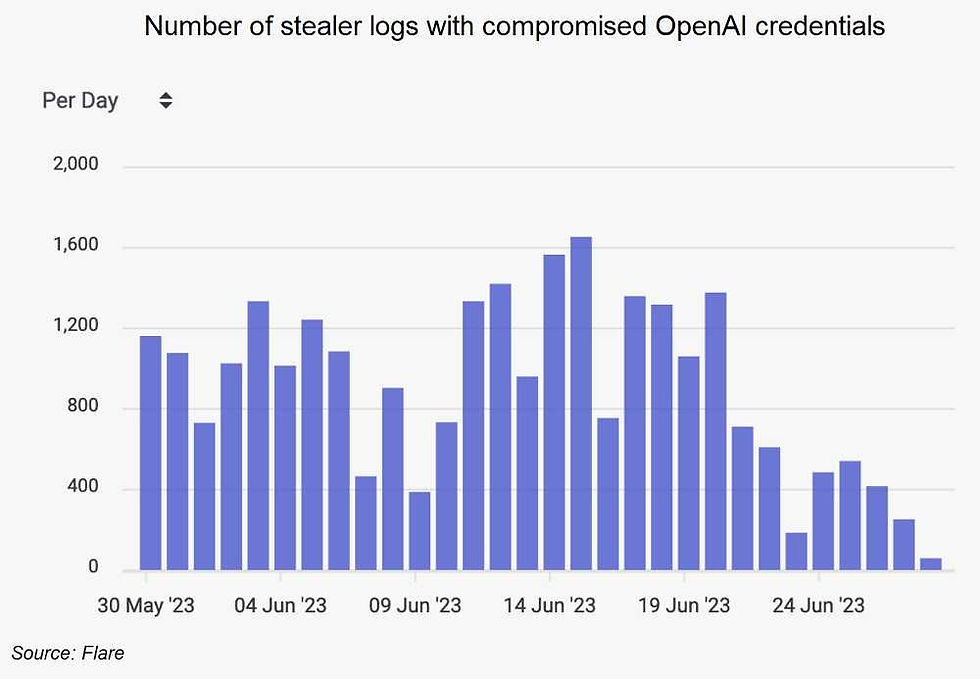
There are places where cybercriminals can purchase information stolen by these families. The report showed that Telegram channels hosted most of these logs (74%), while 25% were found on Russian-speaking marketplaces. Alarmingly, over 200,000 stealer logs contained OpenAI credentials, which is being used more often by businesses. This poses a risk of proprietary information, internal business strategies, and source code being stolen. OpenAI, in case you haven’t heard of them, it’s the research lab that created ChatGPT.
Corporate credentials are highly valuable in the cybercrime underground. By getting these credentials, they can log into corporate services such as SaaS, CRM, and VPN as if they are part of the corporation and deploy stealthy backdoors, install ransomware, or let loose other malware.
Keep up to date: Sign up for our Fraud alerts and Updates newsletter
Want to schedule a conversation? Please email us at advisor@nadicent.com
Comments